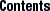Access rights for the four authorization classes are displayed as a list of 16 characters, like this:
r---rmcdr---r--- |
Each character represents a type of access right:
r represents read rights.
m represents modify rights.
d represents destroy rights.
c represents create rights.
- represents no access rights.
The first four characters represent the access rights granted to nobody, the next four to the owner, the next four to the group, and the last four to the world:
Figure 15-1 Access Rights Display

Note - Unlike UNIX file systems, the first set of rights is for nobody, not for the owner.
Default Access Rights
When you create an object, NIS+ assigns the object a default owner and group, and a default set of access rights for all four classes. The default owner is the NIS+ principal who creates the object. The default group is the group named in the NIS_GROUP environment variable. Table 15-6, shows the default access rights.
Table 15-6 Default Access Rights
Nobody | Owner | Group | World |
|---|---|---|---|
- | read | read | read |
- | modify | - | - |
- | create | - | - |
- | destroy | - | - |
If you have the NIS_DEFAULTS environment variable set, the values specified in NIS_DEFAULTS will determine the defaults that are applied to new objects. When you create an object from the command line, you can use the -D flag to specify values other than the default values.
How a Server Grants Access Rights to Tables
This section discusses how a server grants access to tables objects, entries, and columns during each type of operation: read, modify, destroy, and create.
Note - At security level 0, a server enforces no NIS+ access rights and all clients are granted full access rights to the table object. Security level 0 is only for administrator setup and testing purposes. Do not use level 0 in any environment where ordinary users are performing their normal work.
The four factors that a server must consider when deciding whether to grant access are:
The type of operation requested by the principal
The table, entry, or column the principal is trying to access
The authorization class the principal belongs to for that particular object
The access rights that the table, entry, or column has assigned to the principal's authorization class
After authenticating the principal making the request by making sure the principal has a valid DES credential, an NIS+ server determines the type of operation and the object of the request.
Directory. If the object is a directory or group, the server examines the object's definition to see what rights are granted to the four authorization classes, determines which class the principal belongs to, and then grants or denies the request based on the principal's class and the rights assigned to that class.
Table. If the object is a table, the server examines the table's definition to see what table level rights are granted to the four authorization classes, and determines which class the principal belongs to. If the class to which the principal belongs does not have table level rights to perform the requested operation, the server then determines which row or column the operation concerns and determines if there are corresponding row- or column-level access rights permitting the principal to perform the requested operation.
Specifying Access Rights in Commands
This section assume an NIS+ environment running at security level 2 (the default level).
This section describes how to specify access rights, as well as owner, group owner, and object, when using any of the commands described in this chapter.
Syntax for Access Rights
This subsection describes the access rights syntax used with the various NIS+ commands that deal with authorization and access rights.
Class, Operator, and Rights Syntax
Access rights, whether specified in an environment variable or a command, are identified with three types of arguments: class, operator, and right.
Class. Class refers to the type of NIS+ principal (authorization class) to which the rights will apply.
Table 15-7 Access Rights Syntax--Class
Class | Description |
|---|---|
n | Nobody: all unauthenticated requests |
o | The owner of the object or table entry |
g | The group owner of the object or table entry |
w | World: all authenticated principals |
a | All: shorthand for owner, group, and world (this is the default) |
Operator. The operator indicates the kind of operation that will be performed with the rights.
Table 15-8 Access Rights Syntax--Operator
Operator | Description |
|---|---|
+ | Adds the access rights specified by right |
- | Revokes the access rights specified by right |
= | Explicitly changes the access rights specified by right; in other words, revokes all existing rights and replaces them with the new access rights. |
Rights. The rights are the access rights themselves. The accepted values for each are listed below.
Table 15-9 Access Rights Syntax--Rights
Right | Description |
|---|---|
r | Reads the object definition or table entry |
m | Modifies the object definition or table entry |
c | Creates a table entry or column |
d | Destroys a table entry or column |
You can combine operations on a single command line by separating each operation from the next with a comma (,).
Table 15-10 Class, Operator, and Rights Syntax--Examples
Operations | Syntax |
|---|---|
Add read access rights to the owner class | o+r |
Change owner. group, and world classes' access rights to modify only from whatever they were before | a=m |
Add read and modify rights to the world and nobody classes | wn+m |
Remove all four rights from the group, world, and nobody classes | gwn-rmcd |
Add create and destroy rights to the owner class and add read and modify rights to the world and nobody classes | o+cd,wn+rm |